rewrite this content using a minimum of 1000 words and keep HTML tags
Front-running is one of the most debated and ethically challenging issues in crypto trading. In fact, former Binance CEO Changpeng Zhao (CZ) had recently voiced concerns about front-running on DEXs. While the term originates from traditional finance, where it’s considered illegal, front-running in crypto has found new life on the blockchain in more complex and automated forms. This article breaks down what front-running in crypto means, how it works in the crypto space, and how to avoid front-running as a trader.
What Is Front-Running? (Traditional Finance vs. Crypto)
In traditional finance, front-running occurs when a broker uses knowledge of a client’s upcoming large trade to place their own order ahead of it, profiting from the anticipated price shift. Since this involves insider information and breaches fiduciary duty, it’s illegal in most jurisdictions.
But is front-running the same as insider trading? Not exactly. While both involve unethical behaviour, front-running in crypto often exploits blockchain transparency. Anyone can view pending transactions in the mempool (memory pool), where transactions wait before being confirmed. Malicious actors, including miners, validators, or bots, scan this mempool and submit transactions with higher fees to jump the queue and profit from price movements they know are about to occur.
How Does Front-Running Work in Crypto?
Blockchain transparency is a double-edged sword. While it ensures trust and auditability, it also makes every pending transaction visible before it’s confirmed. Here’s how front-running works in crypto:
A large trade is detected in the mempool.
A front-runner submits a similar trade with a higher gas fee to ensure it’s mined or validated first.
The front-runner profits from the resulting price movement, often at the expense of the original trader.
This is especially common on DEXs where there are no centralized intermediaries to prevent such tactics.
MEV in Front-Running
Maximum Extractable Value (MEV) refers to the additional profit that validators, or previously, miners can earn by manipulating the order of transactions within a block. This manipulation includes reordering, inserting, or even excluding transactions to maximize gains. Originally called Miner Extractable Value, the term has evolved with the rise of proof-of-stake (PoS) systems like Ethereum’s, where block producers are no longer miners but validators.
It’s a high-stakes phenomenon that shows how profit incentives can distort fair transaction ordering.
The MEV ecosystem is a complex arena involving multiple players. Validators propose blocks and decide the transaction order. Working alongside them are “searchers” (individuals or teams that develop sophisticated algorithms to scan public mempools for profitable MEV opportunities.) These searchers often deploy automated bots to act on their findings in real-time.
These MEV bots operate with remarkable speed and precision, executing strategies that exploit price discrepancies, arbitrage opportunities, and large DEX transactions. In many cases, they target so-called “whale” trades or high-volume swaps where the potential for front-running or sandwich attacks is most lucrative. Some of the most advanced MEV bots have been reported to earn tens or even hundreds of thousands of dollars each month.
Together, validators, searchers, and bots form an intricate value chain—one that showcases the innovation and equally exposes the risks associated with blockchain transparency.
Common Types of Front-Running Attacks
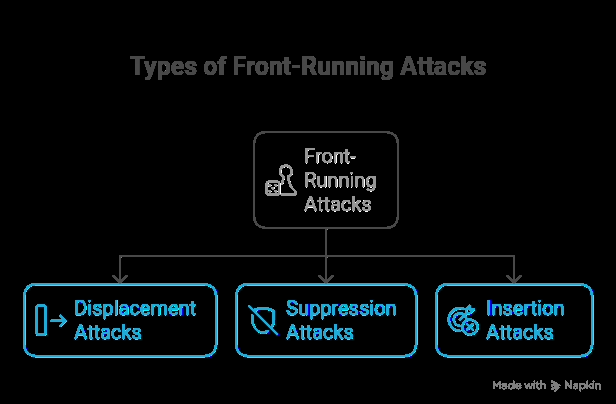
1. Displacement attacks
The attacker observes a pending transaction and submits a competing one with a higher gas fee, pushing the original transaction back in line. The attacker captures the intended opportunity for themselves.
2. Suppression attacks
The front-runner floods the network with high-gas transactions to delay others. This congestion prevents the victim’s transaction from being confirmed in time, resulting in failed or less favourable trades.
3. Insertion attacks (a.k.a. sandwich attacks)
Among the most notorious and harmful forms of front-running in crypto is the insertion attack, commonly referred to as a sandwich attack. This tactic involves strategically placing two trades—one before and one after a victim’s transaction—in order to profit from the resulting price movement.
Here’s how it works: A trader unknowingly submits a large transaction on a decentralized exchange, say a buy order for a specific token. A front-runner, typically an MEV bot or sophisticated trader, detects the pending transaction in the mempool. The attacker quickly places a buy order just ahead of the victim’s transaction, which pushes the token’s price upward. As the original trader’s large buy order executes, it does so at this now-inflated price. Then, almost instantly, the attacker finalizes the attack by placing a sell order, cashing out at the elevated price and capturing the difference as pure profit.
Here’s an example of front running: Imagine a trader is looking to buy a large amount of a DeFi token, say 50,000 units of TokenX, which is currently trading at $2.00 per token. The MEV bot spots this order in the mempool and races to buy TokenX first at $2.00. This initial purchase drives the price up slightly due to the token’s limited liquidity. The trader’s large order then gets filled at the new, higher price, say, $2.05. Immediately afterwards, the bot sells the same tokens it bought earlier at $2.05, making a tidy profit of $0.05 per token, totalling $2,500, all at the expense of the unsuspecting trader.
These attacks are particularly damaging because they manipulate prices in real time, hurt genuine users, and compromise the fairness of decentralized markets. Worse still, since they exploit blockchain transparency and speed rather than hacking or deception, sandwich attacks (a more advanced version of front-running) are difficult to detect and even harder to prevent without proactive protective tools.
Where Front-Running Happens Most
1. Decentralized exchanges (DEXs)
DEXs are among the most common environments for front-running attacks due to their open architecture and public mempools. When a user initiates a trade on DEX platforms, the transaction enters the mempool before being finalized onchain—giving MEV bots time to analyze and exploit the trade. Bots scan for large trades or arbitrage opportunities, then submit their own transactions with higher gas fees to get processed first, effectively “cutting the line” and profiting off the slippage created by the victim’s order.
2. NFT marketplaces with public bidding
Front-running also occurs on NFT platforms, particularly when a high-value bid or listing becomes visible before confirmation. Bots or malicious traders monitor bidding activity and can quickly outbid or snatch NFTs before the original buyer’s transaction is finalized. For example, if someone places a large bid on a rare NFT, an attacker might front-run that bid by offering a slightly higher price with a faster transaction, snagging the asset before the original buyer’s order is processed. This undermines fair market behaviour and erodes trust in NFT platforms.
3. Token launchpads and initial coin offerings (ICOs)
Token launchpads and ICOs are hotbeds for front-running in crypto, especially in the first few moments when a new token becomes available. Bots are programmed to monitor smart contracts and mempool activity so they can rapidly submit buy orders with extremely high gas fees, gaining early access to newly released tokens. This often results in inflated prices before retail users even have a chance to participate. By the time ordinary investors place their trades, the price may have already spiked significantly, forcing them to buy at a premium or miss out entirely.
How to Avoid Front-Running in Crypto
1. Use MEV-resistant tools
To minimize the risk of front-running and sandwich attacks, consider using MEV-resistant tools like Flashbots Protect. These tools offer alternative transaction submission methods that bypass the public mempool—where malicious bots typically scan for exploitable trades. With Flashbots, users can send transaction bundles directly to a private mempool, keeping the details hidden from MEV bots. This secure route helps you avoid front-runners on DEX platforms. It ensures that your transactions are executed without being exposed to opportunistic strategies that could manipulate prices or execution timing.
2. Trade on private or protected DEXs
You can avoid front-running by using private or protected decentralized exchanges like CowSwap and 1inch Fusion implement mechanisms that shield transaction details until they are executed. These platforms act like “dark pools,” preventing malicious actors from using your trade data for front-running attacks. By masking your transaction information until it’s too late for others to act on it, you significantly reduce the risk of manipulation.
3. Set low slippage tolerance
Slippage refers to the acceptable difference between the expected price of a trade and the executed price. By setting a low slippage tolerance, you limit how much a bot can exploit your transaction by pushing the price against you. If a bot tries to manipulate the market, your trade will fail rather than execute at a poor rate, protecting you from inflated costs.
4. Break large trades into smaller batches
Executing a large trade all at once signals your intent to the market, making it easy for bots to target and front-run. Instead, breaking it into smaller chunks reduces visibility and the likelihood of triggering a bot’s algorithm. It also smooths out the price impact, ensuring your average cost remains closer to market value.
6. Avoid trading during high volatility
Periods of high market activity, such as during news announcements or major price swings, attract a swarm of MEV bots looking to capitalize on chaos. Avoiding trades during these volatile windows lowers your chances of being front-run, as fewer bots will be monitoring your activity when things are calmer. Timing can be a powerful defence when navigating unpredictable DeFi waters.
Final Thoughts
Front-running in crypto is a systemic issue deeply tied to blockchain’s open architecture. While the visibility of the mempool fosters transparency, it also exposes traders to exploitation. Understanding how front-running works, recognizing its forms, and using available tools and best practices can help protect your trades.
As the DeFi ecosystem matures, we can expect greater innovation in MEV mitigation and fairer trading infrastructure. But until then, navigating crypto securely requires awareness, the right tools, and a cautious approach.
Disclaimer: This article is intended solely for informational purposes and should not be considered trading or investment advice. Nothing herein should be construed as financial, legal, or tax advice. Trading or investing in cryptocurrencies carries a considerable risk of financial loss. Always conduct due diligence.
If you want to read more market analyses like this one, visit DeFi Planet and follow us on Twitter, LinkedIn, Facebook, Instagram, and CoinMarketCap Community.
and include conclusion section that’s entertaining to read. do not include the title. Add a hyperlink to this website [http://defi-daily.com] and label it “DeFi Daily News” for more trending news articles like this
Source link